Addressing Mobile Operator VoLTE Roaming LI Challenges
This is a busy time for mobile operators, both large and small. The march toward 5G deployment is underway for most large mobile operators while small and mid-size operators are pushing toward the deployment of IP Multimedia Systems (IMS) for Voice over LTE (VoLTE) operation. VoLTE allows operators to phase out 3G voice service by using the LTE network and SIP/RTP Voice over IP technology to provide all-digital services whether voice, data, or SMS. The migration to VoLTE promises to drastically reduce deployment and operational costs.
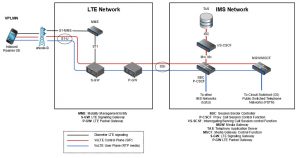
New network architecture deployments also imply new operational, maintenance, and compliance solutions. We will focus on the lawful intercept (LI) for VoLTE networks. Figure 1 below shows a simplified diagram of a typical VoLTE architecture.
FIGURE 1. Simplified LTE, IMS Network
The red line shows the call signaling path between the mobile device and the IMS network. The blue line is the call content between the mobile device and the IMS network. The lawful intercept of VoLTE calls in this scenario is quite straight-forward and there are multiple options:
- Perform passive interception between the S-GW and P-GW by using the S11 and SGi interfaces of the LTE network.
- Perform passive interception on the Mx/Mw interface and the Gm interface in the IMS network.
- Use the lawful intercept interface of the P-CSCF/S-CSCF and MGW equipment (called X interface) to provision the intercept and receive the raw call signaling and content for the intercept target, then mediate the raw output into an industry-standard LI output format like T1.678, ETSI 102 232-5, or 3GPP 33 108.
The selected option depends on scaling, network performance, and security criteria. Yaana provides proven products and services to assist in the deployment of VoLTE LI using any one of these options.
The VoLTE Roaming Lawful Intercept Challenge
Lawful interception of VoLTE traffic becomes very difficult for VoLTE Roaming scenarios – where the subscriber is connected to a visited network and makes or receives VoLTE calls. The reason why LI is difficult in this scenario is that the call involves two networks and the traffic flows between the subscriber on the visited and home networks may be encrypted or may not show up at all!
Most regulators around the world have made the statement that the “visited and home mobile networks must be capable of delivering voice calls to the authorities.” If you are a network operator, this means that if there is a mobile device roaming onto your network, you must be able to perform LI on that device. Likewise, if your subscriber is roaming onto another network, and the subscriber makes a VoLTE call that comes back to your IMS, you must be able to intercept that call.
Local Breakout (LBO) and S8 Home Routing (S8HR)
The 3GPP Specifications have described two ways to support roaming:
- Local Breakout (LBO): This involves the mobile device on the visited network using the IMS of that visited network for the VoLTE calls.
- S8 Home Routing (S8HR): In this case, the mobile device connects back to the IMS of the home network for VoLTE calls.
The local breakout architecture requires the visited network to have an IMS. If the visited network does not have an IMS, the home operator will not be able to provide VoLTE service to their subscribers when roaming, which is a problem. For this reason, the local breakout has largely been discarded as a viable option for VoLTE roaming deployment, and S8HR is the defacto standard for supporting VoLTE roaming. So, let’s take a look at S8HR in a little more detail as it relates to Lawful Intercept.
S8HR and how it works
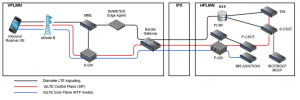
Figure 2 below extends the diagram in Figure 1 to show how the S8HR VoLTE roaming works.
Figure 2. S8HR VoLTE Roaming
In this case, the call signaling of the visiting mobile user (called inbound roamer) terminates at the home network P-CSCF where the SIP signaling performs the call establishment messaging. To further complicate things, the mobile network attaches the process of the inbound roamer, which involves the visited network S-GW connecting to the home network P-GW and this, in turn, connects to the home network IMS.
Now, if you’re the home network, the call signaling terminates in your IMS, so using an X interface or passive probes are possible LI options. However, the call content may not flow back through the home network – it may connect from the border gateway of the visited network directly to the peer device.
If you’re the visited network, it might look like you have a better chance at performing LI – after all, the user is connected to your network and all their traffic is flowing through your LTE network. And the logical point of interception looks to be between the visited network S-GW and the home network P-GW.
Unfortunately, from the LTE network perspective, the SIP/RTP VoLTE traffic is opaque to the LTE network – it’s just another packet context pipe encapsulated in a GTP wrapper going out the network. In this case, the X interface of the LTE network cannot perform LI. However, a probe passively connected to the S5/S8 interface could as long as it can decapsulate the GTP and interpret the SIP/RTP contents inside. And indeed, Yaana has the probe solutions that can do just that.
The complications continue – often the SIP signaling traffic between the mobile device and the P-CSCF is encrypted – and this encryption does not allow the signaling to be passively intercepted in the visited network. However, the RTP is generally not encrypted and it can be intercepted if the IP address and port number of the target are known.
Other methods of LI for Visited Networks
One option being explored is signal redirection – that means if there is an inbound roamer and it’s a target, the visited network would use the signaling inside the LTE network to redirect inbound roamers that are LI targets to terminate inside the visited network. This option involves adding intelligence during the device attach sequence to redirect the device to a P-GW capable of terminating the mobile device on the visited network and the P-CSCF in the home network. By deploying signal redirection, the LI signaling, and call content can be performed at the visited network.
There may also be other reasons why signal redirection is preferred overusing X interfaces even if those X interfaces can perform the intercept. Security is the primary concern here – using an X interface for LI means that the software inside the network element is aware of what intercepts are being performed. These network elements could be compromised in such a way as to deliver this information to external parties that are not allowed or authorized to have this information. Signal redirection and passive probe options eliminate this vulnerability.
Yaana’s VoLTE LI Initiatives
Yaana is a market leader in LI solutions for wired and wireless IP based networks for mobile, fixed, and virtualized network architectures. Yaana has innovative solutions and industry experience to deploy passive probe, active X interface, and signal redirection LI solutions to address VoLTE roaming challenges. Yaana is an active participant in the standards organizations addressing these challenges.
For more information on Yaana’s VoLTE solutions and patented approaches that address VoLTE roaming LI, contact Yaana at info@yaana.com or via our website at www.yaana.com.