New Google Chrome Browser Provides Notice of “Security Weak”
This contribution describes the move toward more secure and trusted websites based on strong digital certificates, CA/browser industry actions, and very recent changes by some browser vendors to enforce the transition away from now depreciated weak certificates.
Outing Weak Certificates
A few days ago, if you were using a browser on a Google Android smartphone or tablet and accessed ETSI’s portal, you would have seen something new and vivid red as part of the URL at the top of the site. If you then tapped on the broken red lock, you would have seen the adjacent notice.
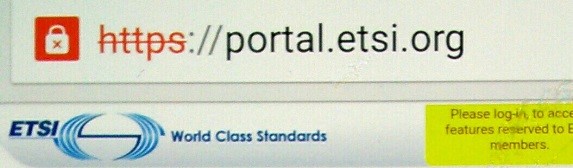
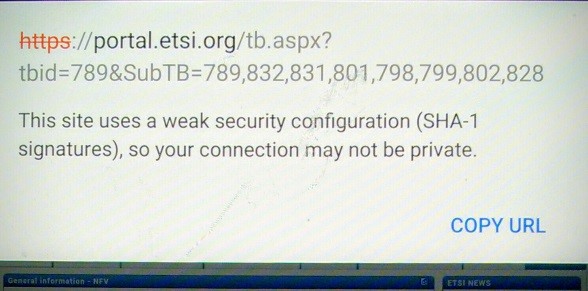
As you browsed to other sites, you would have seen similar notices on a surprising number of them.
This is occurring because browser and operating system vendors working together with the Certificate of Authority community in the CA/Browser Forum have started to move aggressively to improve website security. The CA/B Forum is arguably one of the least known but most powerful global security/trust organizations. The power derives from the reality that they collectively control the browser code, the trusted certificate tables on devices, the assurance criteria for those receiving certificates, and the verification of validity. End users can change some of these parameters themselves, but few except select security communities actually do. Many of the key components are found in Baseline Requirements Documents found at https://cabforum.org/baseline-requirements-documents/
ETSI’s own Electronic Signatures and Infrastructures Technical Committee (TC ESI) has long had a close working relationship with the Forum, and some its specifications are versions of those of the Forum. See, e.g., TS102042, Policy requirements for certification authorities issuing public key certificates.
It is important to note that these certificates are used both for trust (i.e. validating the entity reached at the website is who it asserts itself to be), as well as establishing an encrypted path between the end user and the website server using the TLS protocol and Secure HTTP with the prefix https:// Because this process is also used for transferring software, it is also very important in reducing malware.
The known weakness of SHA-1 led to the “depreciation” of its use within the CA/B community last year with a definitive phasing out timetable. It also set off an energetic debate regarding the extent to which browser vendors should “out” the weak certificates. Any user can query the certificate information in most browsers and see whether they use SHA-1 encryption or not, but few do.
Google Chrome recently took perhaps the most aggressive stance – which has given rise to the new URL appearances. The details together with useful guidance for website developers can be found at Intent to Deprecate: SHA-1 certificates,
https://groups.google.com/a/chromium.org/forum/#!topic/security-dev/2-R4XziFc7A%5B1-25%5D
As a result certs that still use SHA-1 and expire in 2016 will be yellow. Those that expire after 2016 will be red. As Google Chome states: “Using SHA-1 in 2015 is not desirable…By degrading the UI, we wish to provide negative reinforcement that SHA-1 is no longer secure enough, and positive encouragement for CA’s that adopt modern algorithms.” The stated aim is “that SHA-1 will be virtually unused in certificates by 2016, ensuring a smooth removal.”
U.S. White House Action
In part because of significant high-profile cybersecurity vulnerabilities of U.S. government agency systems, on 8 June, the White House issued a directive that establishes a new initiative known as HTTPS-Everywhere for Government. See
https://www.whitehouse.gov/blog/2015/06/08/https-everywhere-government
Unfortunately, the directive sets a rather distant date of 31 Dec 2016, and fails to deal with any of the substantive issues relating to certificate trust or strength. It is not apparent from their consultations that the critical CA/B Forum community was ever involved. A cursory scan of U.S. government websites in fact reveals that many of them are using no certificates at all, and a surprising number are still using SHA-1 encryption. Only one appears to be using what should be the norm – a strong Extended Validation Certificate highlighted by the green hue in the URL area.

Notwithstanding the initial deficiencies, the White House action does establish a valuable initiative that is likely to be widely emulated worldwide.
The Global Situation
Most government agencies and institutions throughout the world seem decidedly deficient in implementing contemporary trust and security technologies for their websites. It is quite edifying to choose some arbitrary national or international organization site – including governmental and intergovernmental ones – and force a https:// connection. Very frequently, there is no certificate use. A surprising number use depreciated SHA-1 encrypted certificates. Almost none use EVcerts – perhaps with the notable exception of the International Telecommunication Union to its credit – due in part to the advocacy of its former ITU-T cybersecurity rapporteur who helped develop the international standards version of the EVcert specification.
What is a highly positive development is that most financial institutions that host sites for account transactions appear to using EVcerts extensively. With the new aggressive “security weak” notifications being pushed out in new browser releases, the situation should quickly improve.
